1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
| #include<stdio.h>
#include<sys/ptrace.h>
#include<stdlib.h>
#include<sys/types.h>
#include<sys/wait.h>
#include<unistd.h>
#include<string.h>
#include<errno.h>
#include<sys/syscall.h>
#include<sys/user.h>
const int long_size = sizeof(long);
void getdata(pid_t child, long addr,char* str,int len){
char * laddr;
int i,j;
union u{
long val;
char chars[long_size];
}data;
i = 0;
j = len/long_size;
laddr = str;
while(i<j){
data.val = ptrace(PTRACE_PEEKDATA,child,addr+i*4,NULL);
memcpy(laddr,data.chars,long_size);
++i;
laddr+=long_size;
}
j = len % long_size;
if(j!=0){
data.val=ptrace(PTRACE_PEEKDATA,child,addr+i*4,NULL);
memcpy(laddr,data.chars,j);
}
str[len]='\0';
}
void putdata(pid_t child, long addr,char* str, int len){
int i,j;
char *laddr;
union u{
long val;
char chars[long_size];
}data;
i = 0;
j = len/long_size;
laddr = str;
while(i<j){
memcpy(data.chars,laddr,long_size);
ptrace(PTRACE_POKEDATA,child,addr+i*4,data.val);
++i;
laddr+=long_size;
}
j = len % long_size;
if(j!=0){
memcpy(data.chars,laddr,j);
ptrace(PTRACE_POKEDATA,child,addr+i*4,data.val);
}
}
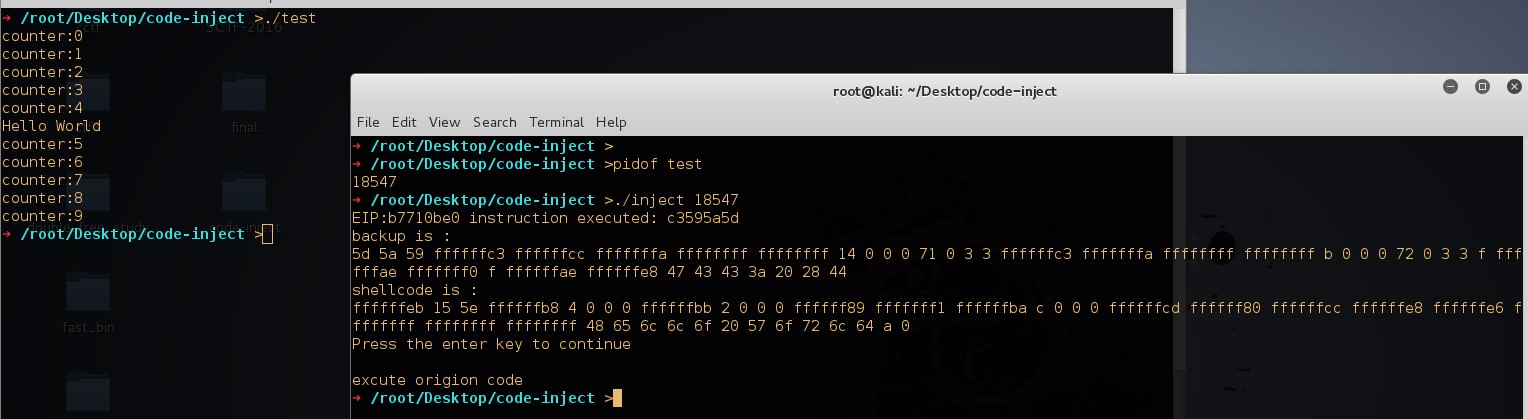
int main(int argc,char*argv[]){
pid_t traced_process;
struct user_regs_struct regs,newregs;
long ins;
int k,h;
int len=41;
char shellcode[] = "\xeb\x15\x5e\xb8\x04\x00\x00\x00"
"\xbb\x02\x00\x00\x00\x89\xf1\xba"
"\x0c\x00\x00\x00\xcd\x80\xcc\xe8"
"\xe6\xff\xff\xff\x48\x65\x6c\x6c"
"\x6f\x20\x57\x6f\x72\x6c\x64\x0a\x00";
char backup[len];
long addr;
if(argc!=2){
printf("command input error\n");
exit(1);
}
traced_process = atoi(argv[1]);
ptrace(PTRACE_ATTACH,traced_process,NULL,NULL);
wait(NULL);
ptrace(PTRACE_GETREGS,traced_process,NULL,®s);
ins = ptrace(PTRACE_PEEKTEXT,traced_process,regs.eip,NULL);
printf("EIP:%lx instruction executed: %lx\n",regs.eip,ins);
getdata(traced_process,regs.eip,backup,len);
printf("backup is :\n");
for(k = 0;k<41;k++){
printf("%x ",backup[k]);
}
printf("\n");
putdata(traced_process,regs.eip,shellcode,len);
printf("shellcode is :\n");
for(k = 0;k<41;k++){
printf("%x ",shellcode[k]);
}
printf("\n");
ptrace(PTRACE_SETREGS,traced_process,NULL,®s);
ptrace(PTRACE_CONT,traced_process,NULL,NULL);
wait(NULL);
printf("Press the enter key to continue\n");
getchar();
putdata(traced_process,regs.eip,backup,len);
ptrace(PTRACE_SETREGS,traced_process,NULL,®s);
printf("excute origion code\n");
ptrace(PTRACE_DETACH,traced_process,NULL,NULL);
return 0;
}
|