Baiudu杯 pwn专场记录
前言
十一月的第一周,百度杯的pwn专场,就去学习了下姿势,更加认识到自己的不足和问题所在,以后努力更正改进~
本次比赛一共是3个misc和三个pwn,题目都不难,pwn好像有两个都是原题,但是我只google到了第二个题目…
1.pwnme
格式化字符串(x64)其实后面还有个bof,fmt和bof的结合可能才是出题人的本意吧(我猜的)。
1 | $ checksec pwnme |
- 格式化字符串
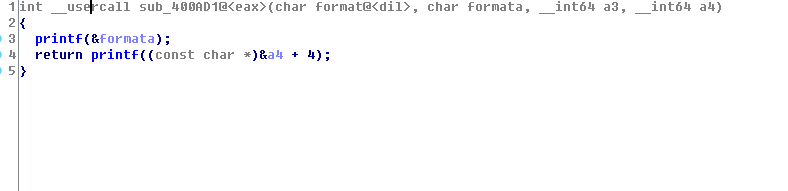
在输出name和pass的时候会导致这个格式化字符串,可以任意地址读写。
但是需要注意
- x64中fmt 泄露的参数的顺序(
RDI-RDX-RCX-R8-R9-stack[0]-stack[1]......) - 因为有00截断,所以要格式化的地址放后面( -。- 没错 后入式)
本来以为开了 Full RELRO 的情况下 DynELF就不行了,还想着手动去解析出libc基地址然后再搞呢…改了下方式就可以了。
在师傅的指导下完成了leak的部分,然后是使用DynELF去泄露system的地址,后面改返回地址为system,然后设置好参数后,ret过去。
1 | # -*-coding:utf-8-*- |
2.loading
简单粗暴把输入的每个字节 /2333.0 然后直接执行浮点数的考察啊…google了下 float shellcode,就找到了原题啊…把别人exp里的1337.0改成2333.0就好了…
搜到了pctf 2016 fixedpoint writeup
还有这个 PlaidCTF 2016 fixedpoint
pctf 这个的源码,简直不要再一样好么。
1 |
|
附上exploit
1 | import struct |
感言
这个比赛让我感觉收获最大的应该是“思考”:要学会自己思考,不然做再多题目都没有用。